How To Lock Usb Drive In Windows Xp
When connecting a new USB device to the computer, Windows automatically detects the device and installs an appropriate driver. As a outcome, the user can almost immediately utilise a connected USB drive or device. In some organizations, the use of USB storage devices (flash drives, USB HDDs, SD cards and then on) is blocked for security reasons to prevent leakage of sensitive data and infecting computers. This commodity describes how to use the Group Policy (GPO) to disable external removable USB-drives.
Contents:
- Configuring GPO to Disable USB Storage Devices on Domain Computers
- Disabling USB Drives via GPO for Specific Users
- Blocking USB and Removable Devices via Registry and Grouping Policy Preferences
- Disable the USB Storage Driver via Registry
- Allow Simply a Specific USB Storage Device to be Connected
Configuring GPO to Disable USB Storage Devices on Domain Computers
In all versions of Windows, starting from Windows 7, you tin flexibly manage access to external drives (USB, CD / DVD, floppy, tape etc.) using Group Policies (we are not considering a radical way to disable USB ports through BIOS settings). Information technology is possible to programmatically cake the use of simply USB drives, without affecting such USB devices as a mouse, keyboard, printer, etc (which are not recognized as a removable disk).
The USB device blocking policy volition piece of work if the infrastructure of your Advertizing domain meets the following requirements:
- Active Directory schema version — Windows Server 2008 or newer;
Note. The prepare of Group Policies allows to control the installation and use of removable media on Windows appeared only in the Ad version 44.
- Desktop OSs –Windows seven or newer.
We are going to restrict the use of USB-drives for all computers in a certain Advert container (OU). Yous can apply the USB block policy to the unabridged domain, but this volition touch on the servers and other technological devices. Allow's assume that nosotros desire to apply the policy to OU named Workstations. To do it, open the GPO management panel (gpmc.msc), correct-click on OU Workstations and create a new policy (Create a GPO in this domain and Link information technology here.)
Tip. In case of stand-alone reckoner, the USB-device restriction policy can be edited using a local Group Policy Editor – gpedit.msc. Local Group Policy Editor is no available in the Windows Home editions, simply yous tin can install it like this: How to enable gpedit.msc on Windows 10 Abode.
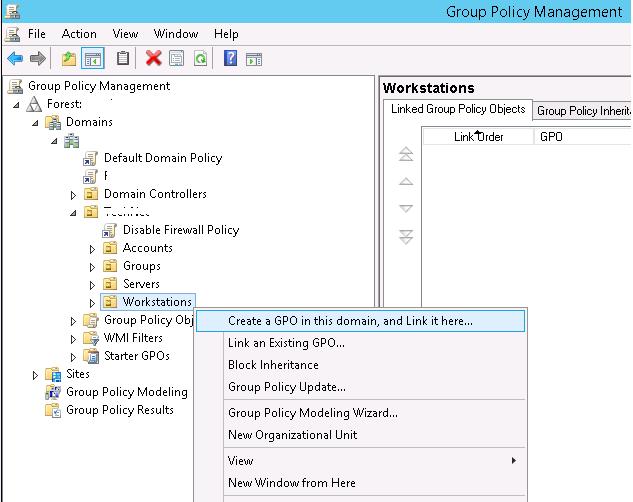
Prepare the GPO name "Disable USB Access".
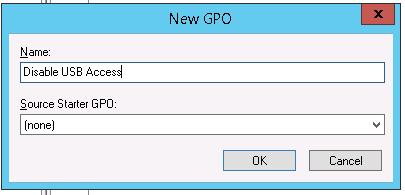
Modify the GPO settings (Edit).
The settings for blocking external storage devices are bachelor in both the User and Reckoner sections of the GPO:
- User Configuration -> Policies -> Administrative Templates -> System -> Removable Storage Access.
- Reckoner Configuration -> Policies -> Administrative Templates -> Organization -> Removable Storage Admission.
If you want to cake USB storage devices for all reckoner users, y'all need to configure the settings in the "Computer Configuration" section.
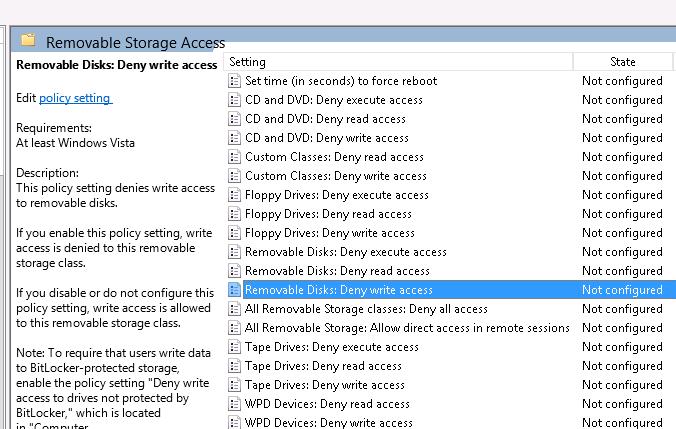
In the Removable Storage Access department, there are several policies allowing yous to disable the use of dissimilar types of storage classes — CD/DVDs, FDD, USB-devices, tapes, etc.
- CD and DVD: Deny execute admission.
- CD and DVD: Deny read admission.
- CD and DVD: Deny write access.
- Custom Classes: Deny read access.
- Custom Classes: Deny write access.
- Floppy Drives: Deny execute access.
- Floppy Drives: Deny read access.
- Floppy Drives: Deny write admission.
- Removable Disks: Deny execute access.
- Removable Disks: Deny read access.
- Removable Disks: Deny write access.
- All Removable Storage classes: Deny all access.
- All Removable Storage: Allow direct access in remote sessions.
- Tape Drives: Deny execute admission.
- Tape Drives: Deny read admission.
- Record Drives: Deny write access.
- Windows Portable Device – this form includes smartphones, tablets, players, etc.
- WPD Devices: Deny write access.
As you tin run into, you can deny the launch of executable files for each device class (protect computers against viruses), prohibit reading data and writing /editing files on external media.
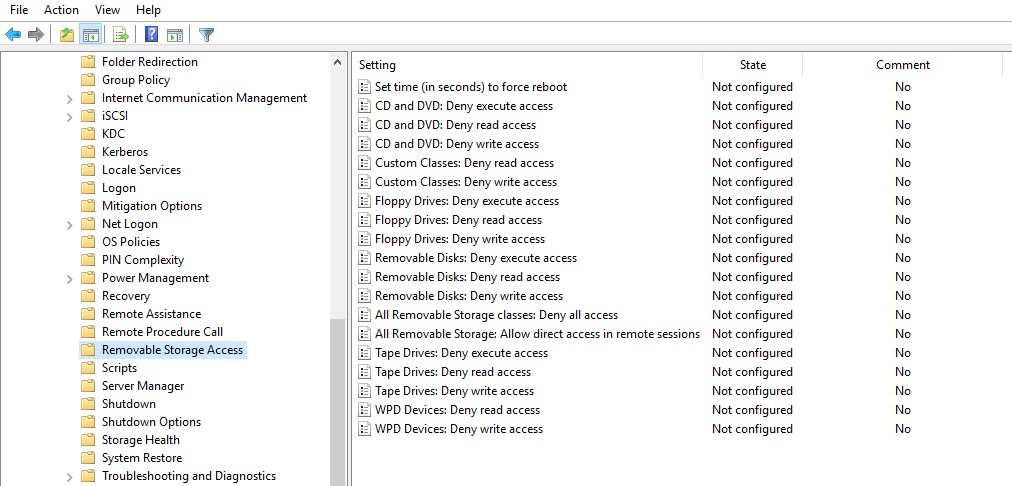
The "strongest" restrict policy — All Removable Storage Classes: Deny All Admission – allows to completely disable the access to all types of external storage devices. To turn on the policy, open information technology and check Enable.
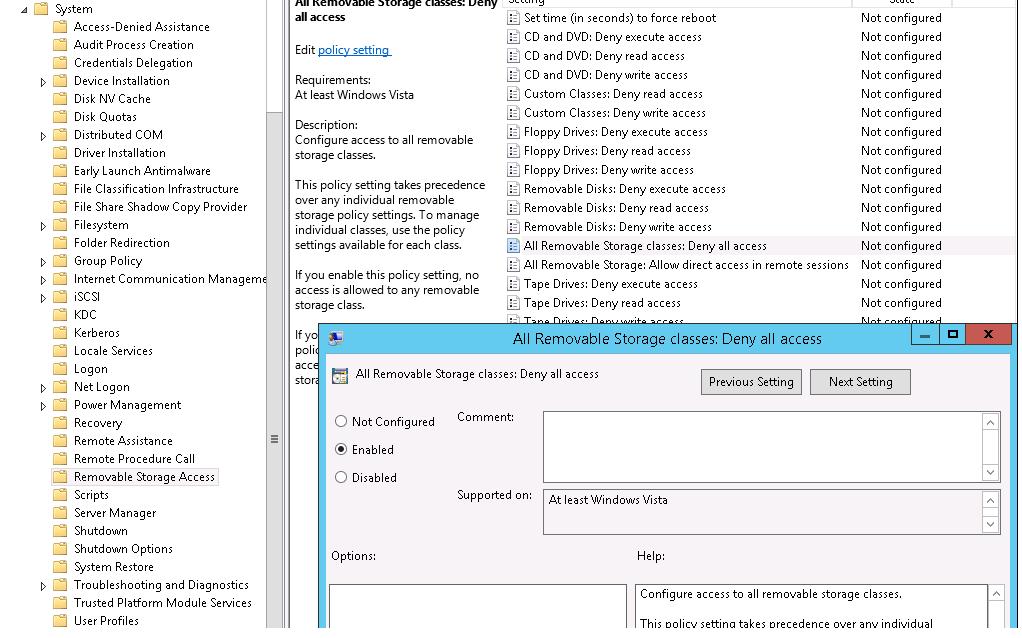
After enabling and updating the policy on client computers (gpupdate /force), the OS detects the continued external devices (non only USB devices, but also any external drives), but when trying to open up them, an error is appeared:
Location is not bachelor Bulldoze is not accessible. Admission is denied.
Tip. The same restriction can exist fix using the registry past creating DWORD parameter Deny_All with the value 00000001 in the registry key HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\RemovableStorageDevices.
In the same policy section, you can configure more flexible restrictions on the use of external USB drives.
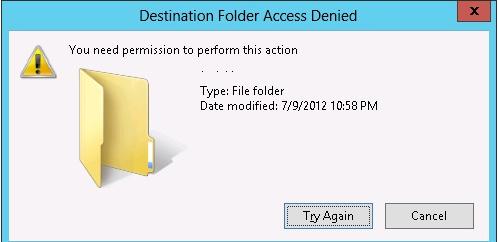
For example, to prevent writing data to USB wink drives and other types of USB drives, you should enable the policy Removable Disk: Deny write access.
In this instance, users will exist able to read the information from the USB wink drive, but when they attempt to write data to it, they will receive an access denied error:
Destination Folder Admission Denied You need permission to perform this activeness
Y'all tin can prevent executable and script files from running from USB-drives using the Removable Disks: Deny execute admission policy.
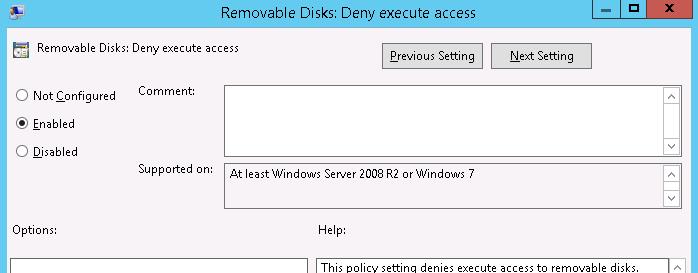
Disabling USB Drives via GPO for Specific Users
Quite often it is necessary to cake USB drives for all users in the domain except administrators.
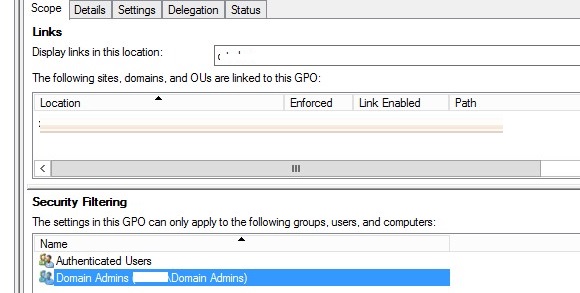
The easiest way to exercise this is to use the Security Filtering in the GPO. For case, to prevent the USB cake policy from existence practical to the Domain Admins group:
- Select your Disable USB Access policy in the Group Policy Management console;
- In the Security Filtering section, add the Domain Admins group;
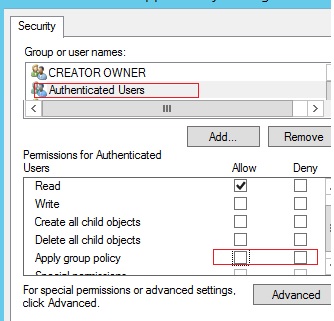
- Go to the Delegation tab and click the Advanced. In the security settings editor, specify that the Domain Admins group is not allowed to apply this GPO (Utilize group policy – Deny).
There may be another job – you need to allow the utilize of external USB drives for everyone except a certain group of users. Create a security group "Deny USB" and add this grouping in the security settings of the GPO. For this group, set permissions to read and apply the GPO, and leave only read permission for the Authenticated Users or Domain Computers grouping (by unchecking the Apply group policy checkbox).
Blocking USB and Removable Devices via Registry and Group Policy Preferences
Yous tin can more flexibly control admission to external devices by configuring the registry settings that are set by the policies discussed to a higher place via the Group Policy Preferences (GPP). All the in a higher place policies stand for to certain registry keys in the HKLM (or HKCU) \SOFTWARE\Policies\Microsoft\Windows\RemovableStorageDevices central (past default this registry cardinal is missing).
To enable one of these policies, you must create a new subkey in the specified primal with the proper noun of the device class you want to cake admission to (column 2) and REG_DWORD parameter with constraint type (Deny_Read, Deny_Write or Deny_Execute). If the value of this parameter is equal to 1, the USB brake is agile, if 0 – there are no recstrcition on this device form.
| Policy proper name | Device Class GUID | Registry parameter name |
| Floppy Drives: Deny read access | {53f56311-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Read |
| Floppy Drives: Deny write access | {53f56311-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Write |
| CD and DVD: Deny read access | {53f56308-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Read |
| CD and DVD: Deny write access | {53f56308-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Write |
| Removable Disks: Deny read admission | {53f5630d-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Read |
| Removable Disks: Deny write access | {53f5630d-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Write |
| Tape Drives: Deny read access | {53f5630b-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Read |
| Record Drives: Deny write access | {53f5630b-b6bf-11d0-94f2-00a0c91efb8b} | Deny_Write |
| WPD Devices: Deny read access | {6AC27878-A6FA-4155-BA85-F98F491D4F33} {F33FDC04-D1AC-4E8E-9A30-19BBD4B108AE} | Deny_Read |
| WPD Devices: Deny write access | {6AC27878-A6FA-4155-BA85-F98F491D4F33} {F33FDC04-D1AC-4E8E-9A30-19BBD4B108AE} | Deny_Write |
You lot can manually create the specified registry keys and parameters. In the screenshot below, I've created a RemovableStorageDevices cardinal, and a subkey named {53f5630d-b6bf-11d0-94f2-00a0c91efb8b}. With the assist of REG_DWORD parameters, I prohibited writing and running executable from USB drives.
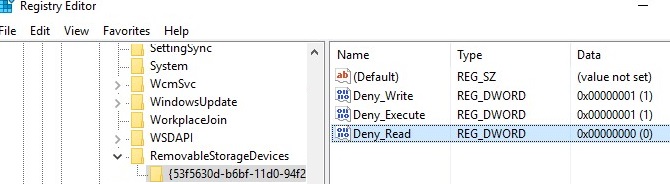
Disabling USB storage will take effect immediately later the policy is applied (no demand to restart your computer). If a USB flash drive is connected to the computer, it will be available until it is reconnected.
You can apply these registry keys and GPP's Item-level targeting to flexibly apply policies that restrict the employ of external USB storage devices. You can utilize policies to specific AD security groups, sites, OS versions, OUs (y'all can use even WMI filters). For instance, yous can create the Storage-Devices-Restrict domain grouping and add the computer accounts for which you want to restrict the apply of USB drives. This group is specified in your GPP policy in the Particular Level Targeting -> Security Group section with the Computer in Group option. This will employ the USB blocking policy to computers that are added to this AD group.
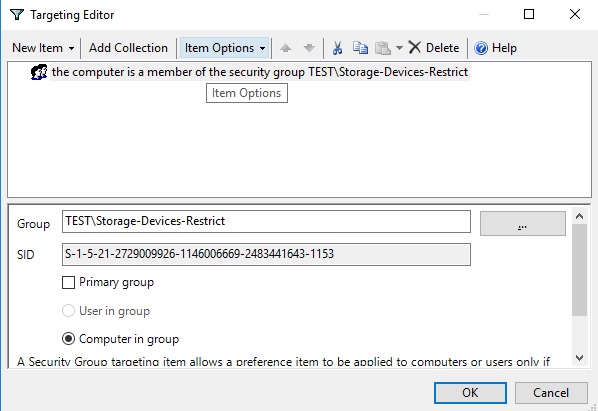
Notation. Similarly, yous can create your ain policies for device classes that are not listed in this list. You can find out the device class ID in the driver properties in the value of the Device Grade GUID attribute.
Disable the USB Storage Driver via Registry
You can completely disable the USBSTOR (USB Mass Storage Driver) driver, which is required to correctly detect and mount USB storage devices.
On a stand-alone computer, yous tin disable this driver by changing the value of the Start registry parameter from 3 to 4. You can practise this through PowerShell:
Set-ItemProperty "HKLM:\SYSTEM\CurrentControlSet\services\USBSTOR" -proper name Get-go -Value 4
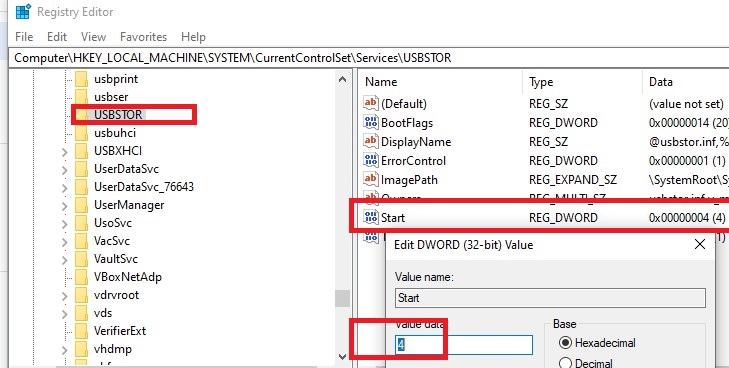
Restart your figurer and endeavor to connect your USB storage device. Now information technology shouldn't announced in File Explorer or Deejay Direction panel, and in Device Manager you will see a device driver installation error.
Annotation. This is the merely fashion to disable USB drives in outdated Windows XP/Windows Server 2003, since in these versions there are no dissever Group Policy settings to restrict access to external USB devices.
You can disable the USBSTOR commuter from running on domain computers using Group Policy Preferences. To do this, y'all need to make changes to the registry through the GPO.
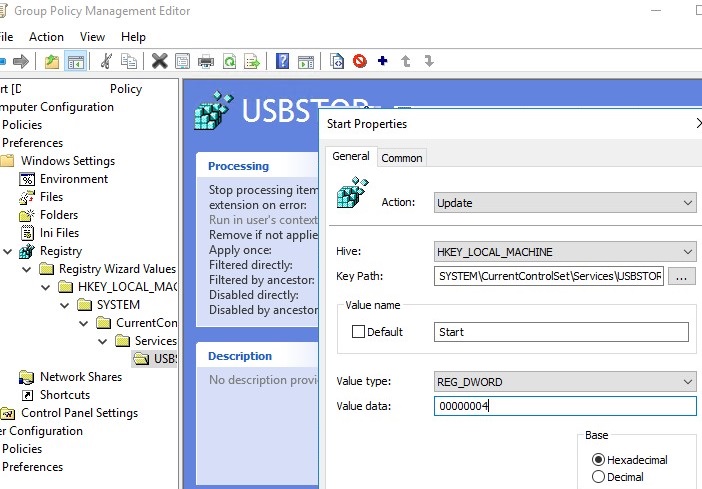
These settings tin exist deployed to all domain computers. Create a new Group Policy, link information technology to the OU with computers and in the Computer Configuration -> Preferences -> Windows Settings -> Registry department, create a new parameter with the values:
- Action: Update
- Hive: HKEY_LOCAK_MACHINE
- Central path: Arrangement\CurrentControlSet\Services\USBSTOR
- Value name: Commencement
- Value type: REG_DWORD
- Value data: 00000004
Allow Only a Specific USB Storage Device to be Continued
You can employ a certain registry setting to allow a specific (approved) USB storage bulldoze to connect to your reckoner. Allow'due south have a quick await at how this can be configured.
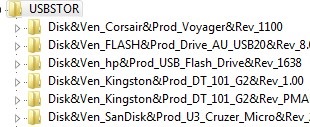
When yous connect any USB storage device to the computer, the USBSTOR driver installs the device and creates a separate registry key under theHKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\USBSTOR. This registry key contains information virtually the USB drive (for example, Disk & Ven_Kingstom & Prod_DT_1010_G2 & Rev_12.00).
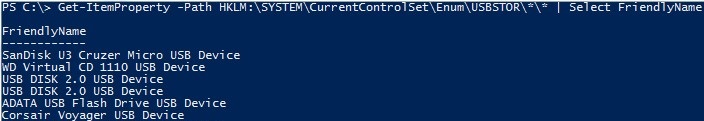
You can list the USB drives that take ever been connected to your figurer with the following PowerShell command:
Become-ItemProperty –Path HKLM:\System\CurrentControlSet\Enum\USBSTOR\*\*| select FriendlyName
Yous tin delete all registry keys for previously connected USB flash drives, except for those you need.
And so yous need to change the permissions on the USBSTOR registry fundamental so that anybody (including System and administrators) has merely read permissions. As a event, when you connect any USB drive, except the immune one, Windows won't be able to install the device.
Source: http://woshub.com/how-to-disable-usb-drives-using-group-policy/
Posted by: horowitzwaston.blogspot.com

0 Response to "How To Lock Usb Drive In Windows Xp"
Post a Comment